We’ve all been there.
For those wanting to play this as a game, there is this wonderfully fiendish website.
https://neal.fun/password-game/
Rule 13 Your password must include the current phase of the moon as an emoji.
I’ve seen this but with a final message of “Sorry, that password is already in use by user about2getOwned@gmail.com.”
Fun fact: password controls like this have been obsolete since 2020. Standards that guide password management now focus on password length and external security features (like 2FA and robust password encryption for storage) rather than on individual characters in passwords.
For today’s 10,000 who have never seen it, https://xkcd.com/936/ succinctly explains why the whole mixed character types thing isn’t favoured.
I’m still waiting on an XKCD that references #936 with the fact that we soon as we have reliable, functional quantum computing, all of the passwords from before that point in time will be completely and utterly broken. That the only way to make a password that a quantum computer would have a tough time breaking is if it was made by another quantum computer. Unless of course the comic has already been made and I just missed it, which is a complete possibility because this year for me has been utterly crap.
soon as we have reliable, functional quantum computing
Which we’ve been told is right around the corner for decades. The issue is that QC doesn’t scale up. If you try you get vastly more noise than signal. Current work in QC is all aimed at reducing that noise, but even for only 70 qbits, the current state of the art can’t eliminate enough of the noise for QC to be useful in most applications.
The only places it’s currently bearing any fruit is where all of the extra work to reduce noise and the delays that incurs are irrelevant because there is no classical approach at all. But even then, the costs are enormous and the benefits are miniscule.
Since 2017 at least; and IIRC years before that; that’s just the earliest NIST publication on the subject I could find with a trivial Web search.
https://pages.nist.gov/800-63-3/sp800-63b.html
Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
“Memorized secrets” means classic passwords, i.e. a one-factor authentication through a shared secret presumed to be known to only the right person.
I wouldn’t say obsolete because that implies it’s not really used anymore. Most websites and apps still use validation not too dissimilar from the OP, even if it goes against the latest best practices.
Yeah, the most recent one for me was creating a password at lemmy.world
I wouldn’t say obsolete because that implies it’s not really used anymore.
I’m not sure where you heard someone use the word “obsolete” that way, but I assure you that there are thousands if not millions of examples of obsolete technologies in constant and everyday use.
My absolute favourite is when your password is too long but they don’t tell you that, I guess because they weren’t expecting it. It only causes a hitch when you later try to login and it doesn’t let you …
Sorry, that password is already in use
BIG red flag. Abort. Abort.
Also I love when they only support certain special characters. So the psuedo random noise created by my password generator won’t work until I curate out the unsupported characters.
I too love the Password game! Please save Paul! ~I truly care about him!~ Truly!
(Sorry, I sometimes like to post really bad comments…)
Sorry, you must have a special character. Oh... Not THAT special character, it has to be a special special character, that one isn't valid. Ah, no, that one's too long. It should be shorter. It needs to be between 11 and 11.5 characters.Half the time I now just enter random nonsense until it lets me create an account. Then, when I want to access a website/app again, I just ‘forget’ my password and reset it to some other random nonsense.
That password is already in use by user ‘gigachad’.
Password can’t exceed 32 characters
Garbage
You think that’s bad, a decade ago I had to use a government-run website that required passwords be exactly 8 characters
that password is already in use
lmao, “security” moment
Brute force user names instead of password. Big Brian moment
Large Brian Moment, for real
The worst one is when it only supports up to like 16 characters but doesn’t tell you so it will only use the first 16 characters and ignore the rest. The next time you need to enter it and get the 64 character password from your password manager it will just say it incorrect and you’re left with no idea on why it’s wrong.
Holy shit you might have just explained why I have to reset my password every time for a local fast food joints own website
So secure even you don’t know the password. It’s like built in MFA.
Looks like someone’s been playing the password game https://neal.fun/password-game/
That game made me want to punch.
My favorite, though, is:
types in password “Password incorrect” goes to reset password “please enter a new password” types in password “your new password cannot be the same”
That just means you entered it wrong the first time.
It often means that one could have derived the correct password from the set of rules - but those rules are not shown when asking for the old password
Exactly this. I want to normalize showing the password requirements when you don’t immediately get the password - if you made me jump through hoops the first time, at least remind me what they were!
The worst part is that if they know that password is already in use… then they aren’t storing their passwords appropriately.
You could store the passwords as hashes and just compare the hashed value.
“Sorry, that password is already in use” ruins it for me. That’s not a realistic message to receive.
Maybe “Your password cannot be one you’ve used previously”.
It follows the vein of some of the password rules and feedback reducing security itself. Like why disallow any characters or set a maximum password length in double digits? If you’re storing a hash of the password, the hash function can handle arbitrary length strings filled with arbitrary characters. They run on files, so even null characters need to work. If you do one hash on the client’s side and another one on the server, then all the extra computational power needed for a ridiculously long password will be done by the client’s computer.
And I bet at least one site has used the error message “that password is already in use by <account>” before someone else in the dev team said, “hang on, what?”.
Should be: “your password cannot be one of your last 24 passwords”
Especially for those places that want your password changed every two weeks.
Should say by who. :)
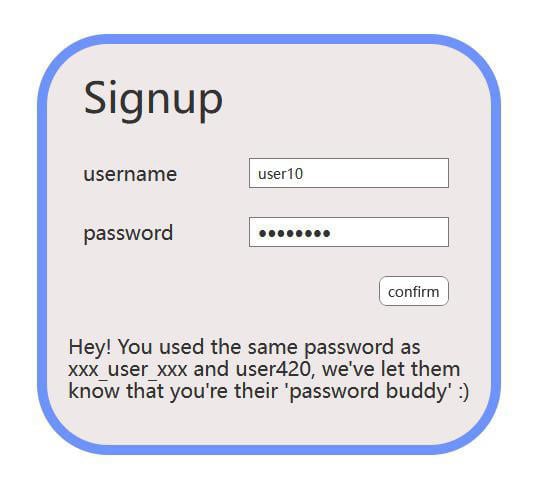
Now we are talking :)